In the modern work environment, real-time communication and information delivery are crucial. To better meet this demand, an increasing number of companies are adopting OsMonitor computer monitoring software to send instant notifications, aiming to enhance work efficiency and team collaboration. Let's delve into this functionality.
Firstly, let's explore the benefits of using instant notifications:
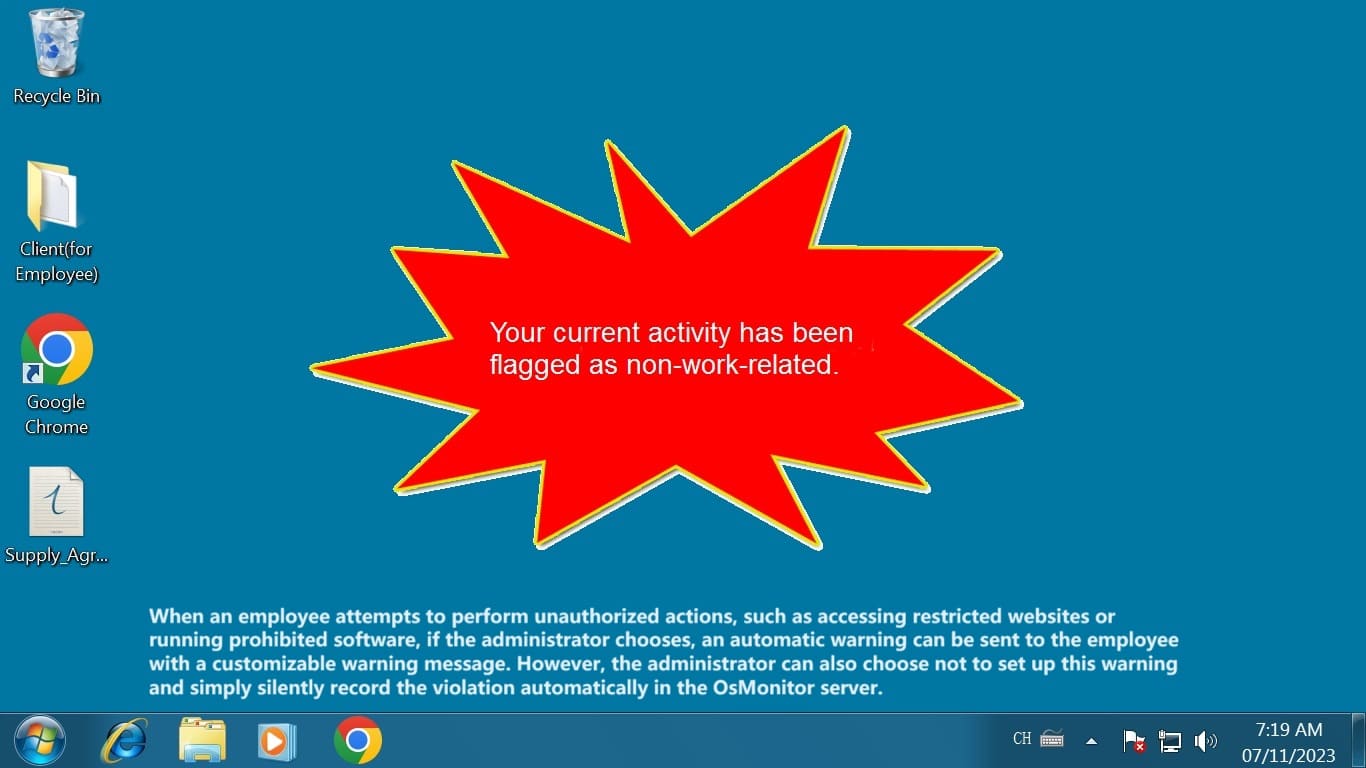
- Instant communication, improved work efficiency: Sending notifications with OsMonitor computer monitoring software allows you to convey important information to your team members promptly. This straightforward, immediate communication method prevents information lag and misunderstandings, resulting in a direct boost in work efficiency! Whether it's project changes, urgent tasks, or important reminders, it enables quick communication, keeping everyone well-informed about the work status.
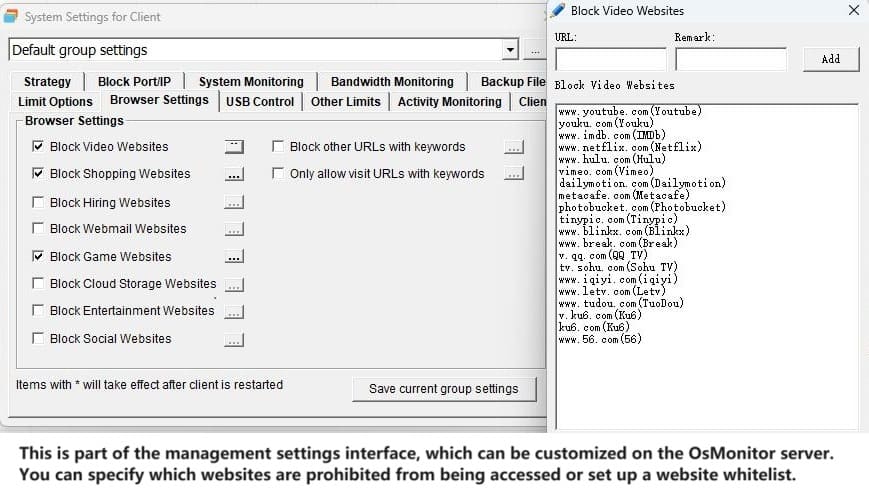
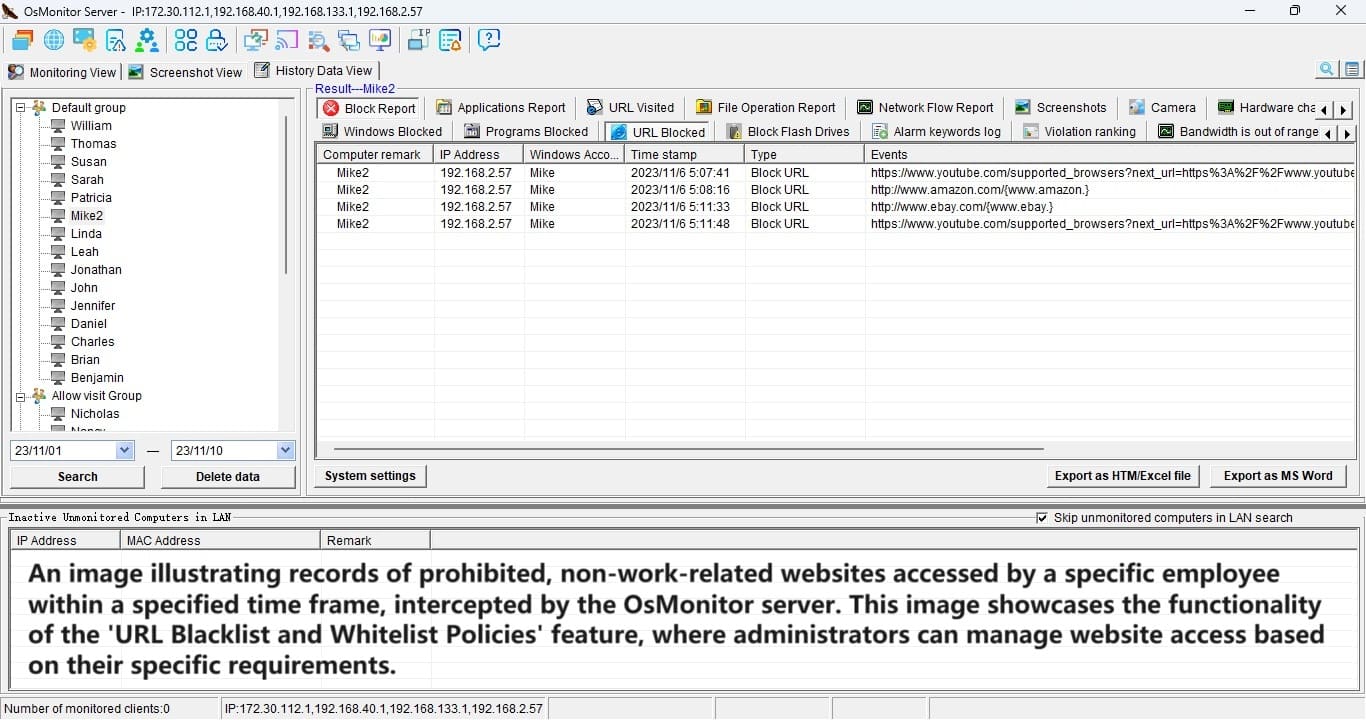
- Targeted delivery, precise communication: The notification feature of OsMonitor computer monitoring software enables you to send messages with precision. With a simple operation, you can choose to send notifications to all employees or colleagues in a specific department. This ensures that information is not scattered, ensuring each person receives only relevant notifications related to their work, making communication more accurate.
- Simple operation, reduced communication costs: OsMonitor computer monitoring software for instant notifications has a straightforward operation. Just click a few buttons in the monitoring view, fill in the message, and you're done. This intuitive and user-friendly approach reduces communication costs significantly, eliminating the need for complex steps and training.
Now, let's see how to send instant notifications through OsMonitor computer monitoring software:
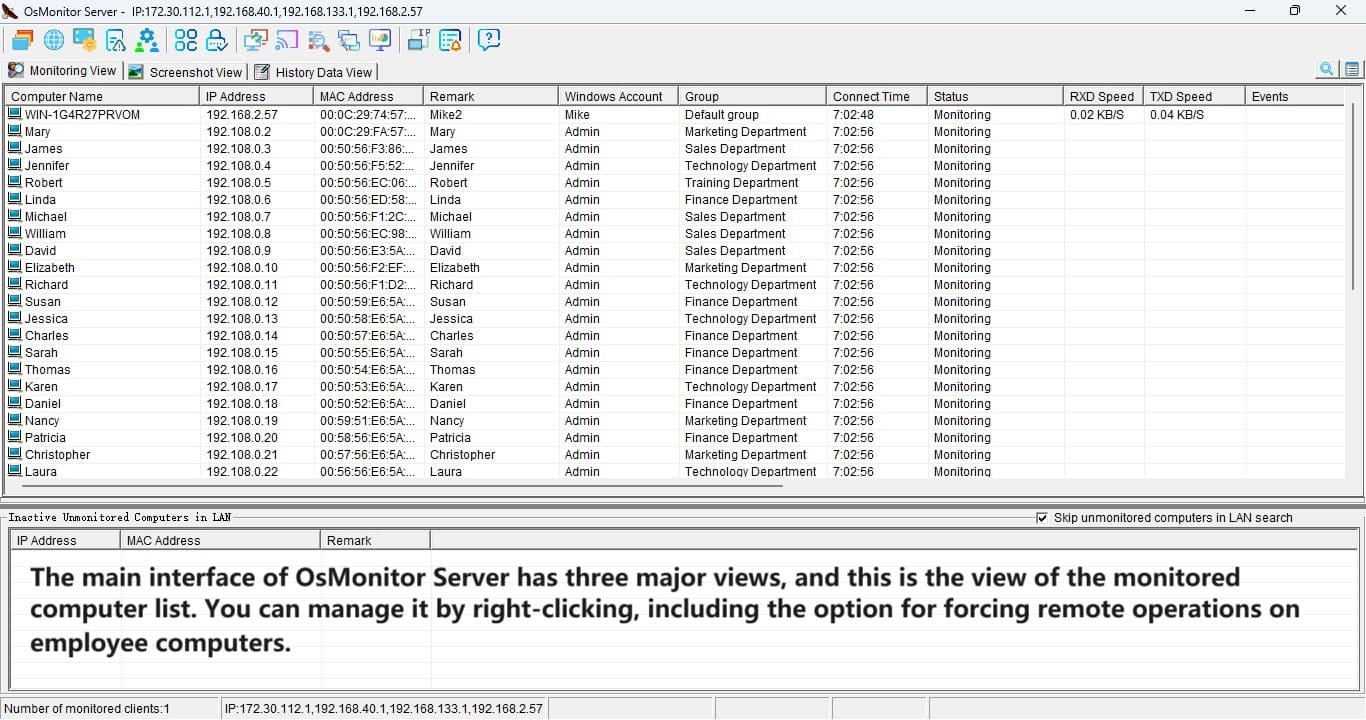
- Open the monitoring software: In the OsMonitor computer monitoring software, open the Management Expert monitoring view, ensuring that the management end is properly connected to the client end.
- Select the target: Managers can choose the recipients for notifications, whether it's all employees or specific department staff. This selectivity adds flexibility to notifications.
- Fill in the message content: When preparing to send a notification, managers need to fill in the message content, ensuring clarity and conciseness for quick understanding by recipients.
- Click Send: After filling in the information, managers only need to click the send notification button to transmit the message to the target users. When sending notifications to multiple recipients simultaneously, the message can be sent to all of them at once.
Through these steps, the instant notification feature of OsMonitor computer monitoring software not only streamlines the management process and improves work efficiency but also makes information delivery more visual and timely. This advanced management approach provides businesses with better means, helping bosses coordinate team work more effectively and enhance overall productivity.