On October 5, 2021, Microsoft released Windows 11 and users can choose to upgrade to the new version for free. To ensure that our customers have a smooth experience with OsMonitor after the Windows 11 upgrade, our team launched a new version of OsMonitor almost simultaneously upon the release of Win 11.
The latest OsMonitor upgrade has been optimized for Windows 11 to provide the best experience for our users. The software interfaces were simplified, and new icon designs were implemented, such as rounded corners of the interface, new typography, and new color palettes. Major updates were made for log retrieval on the server and the warning message prompt windows. In addition, we also tested OsMonitor client compatibility in Windows 11 and made several optimizations to bring our customers a client program with less CPU usage and even better stability.
It has been over a decade since OsMonitor was first released. We’ve come a long way from back then when Windows 98 was the main system, and we will keep developing OsMonitor, the monitoring software for companies and businesses with the need for monitoring employees to ensure work efficiency. Currently, OsMonitor is compatible with Windows 11, Windows XP, Windows 7, Windows 10, and all computers with a Windows system.
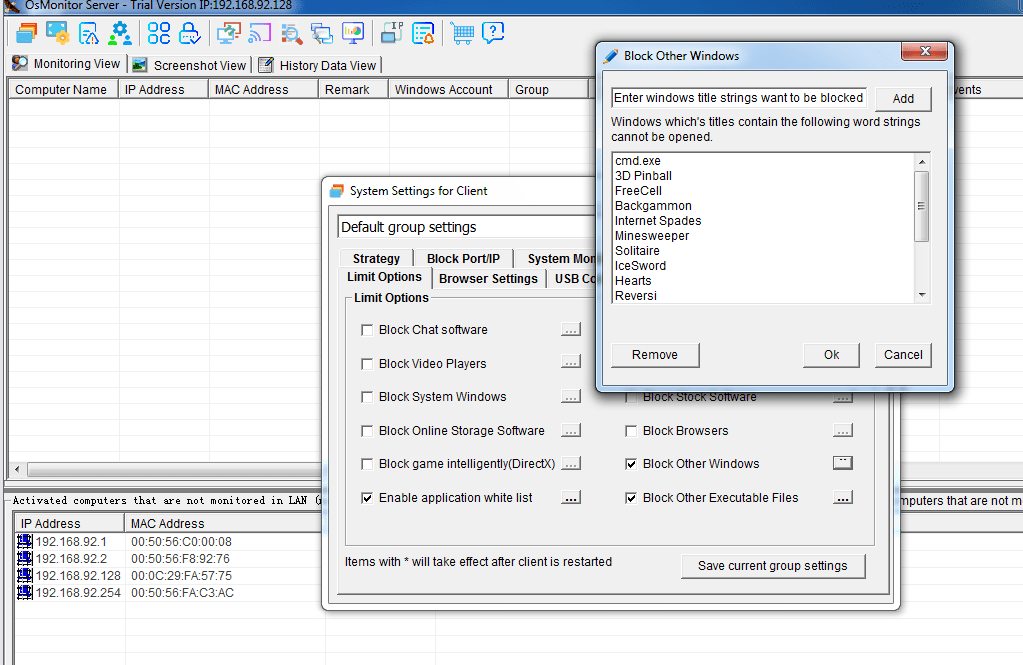
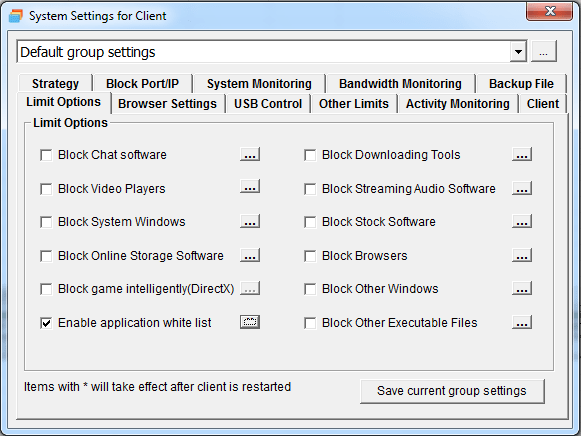
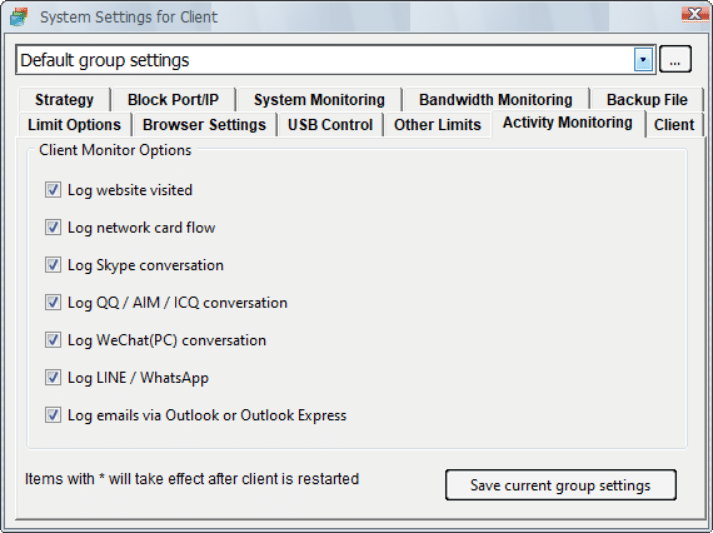
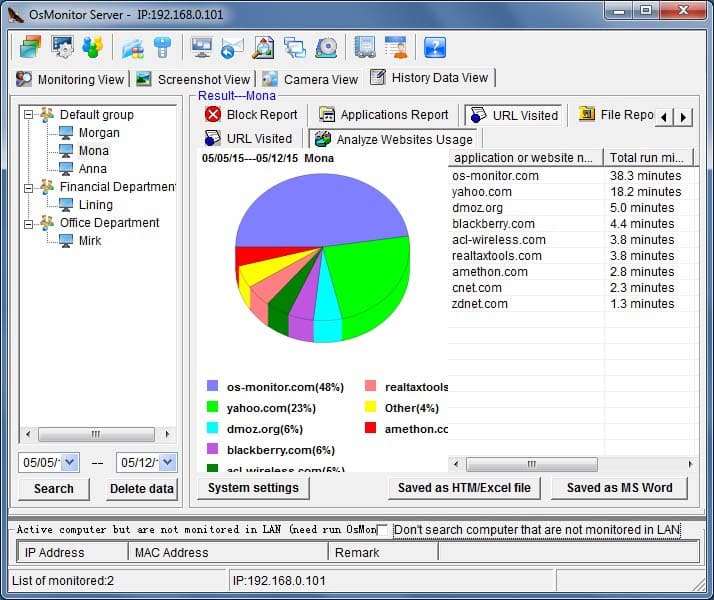
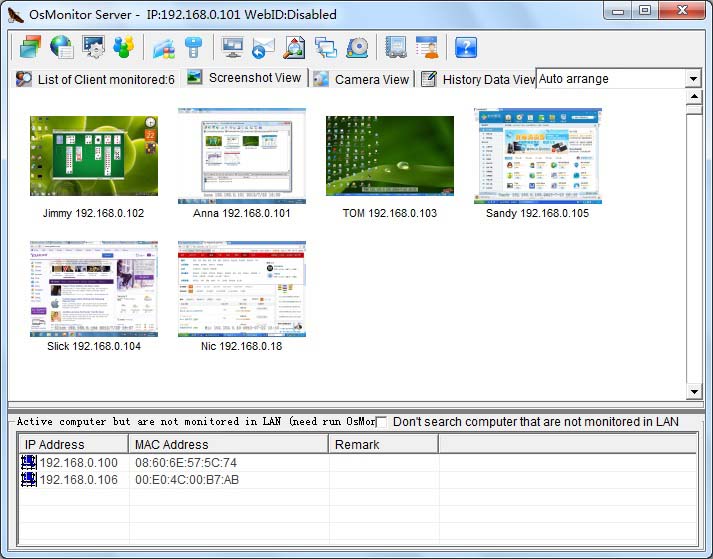
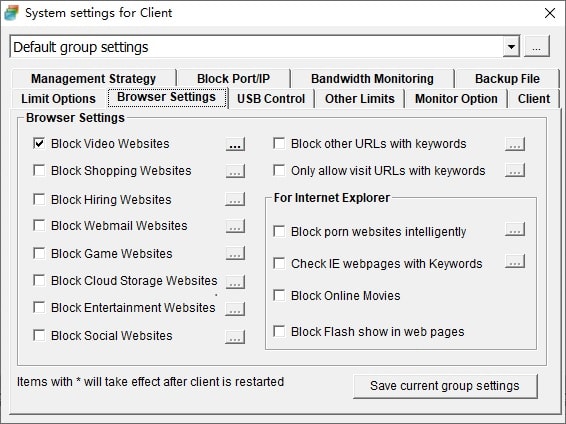
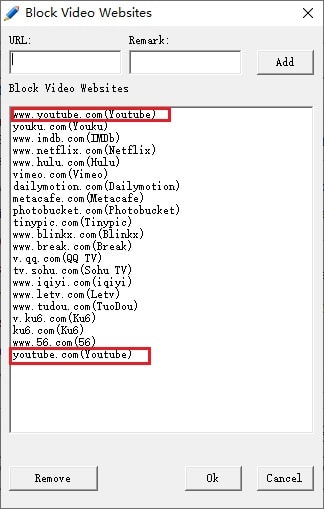
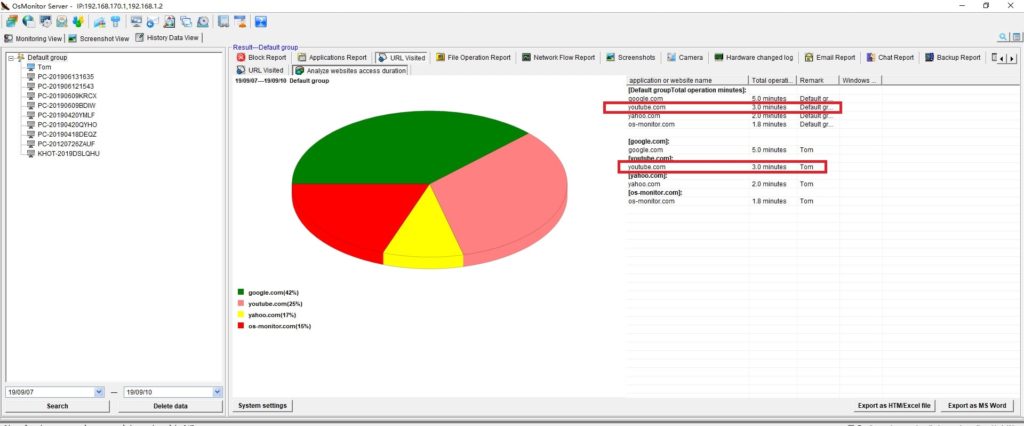
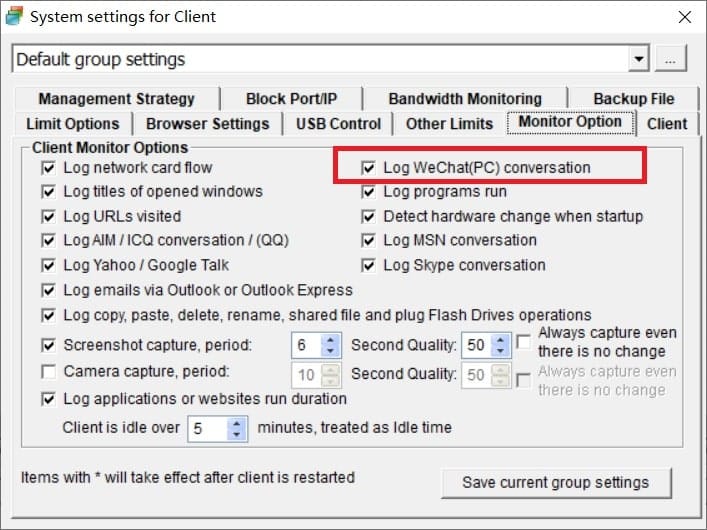
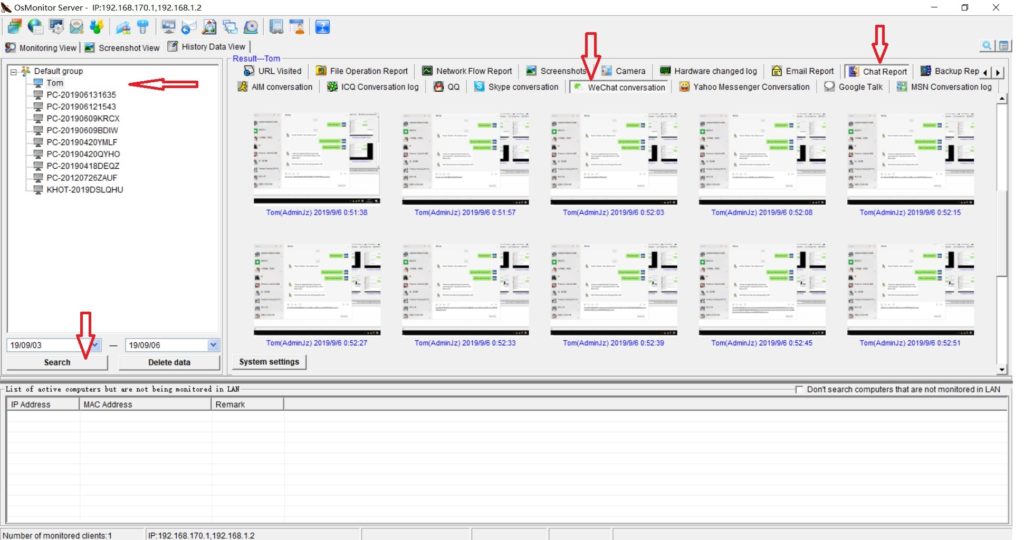
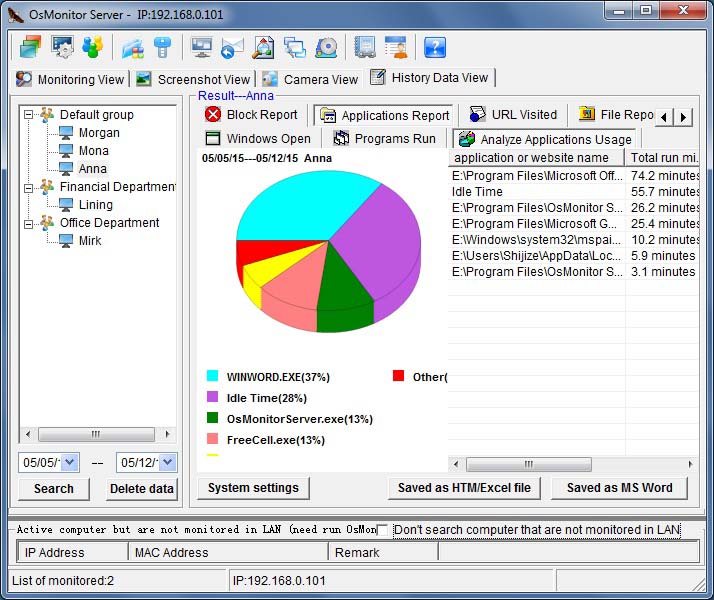
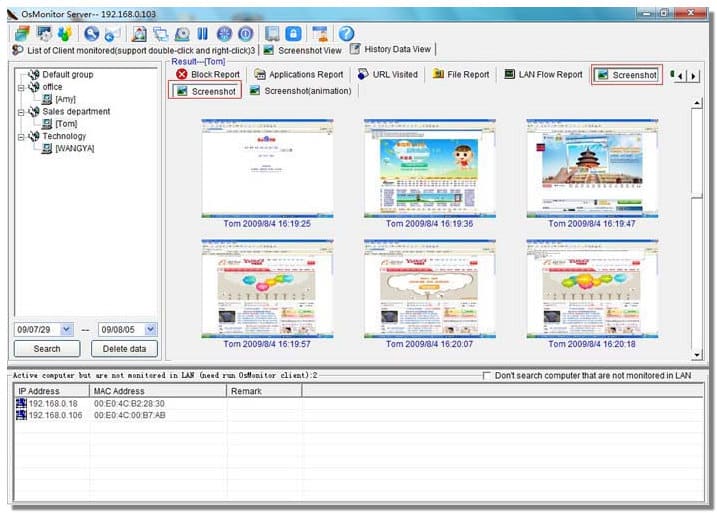
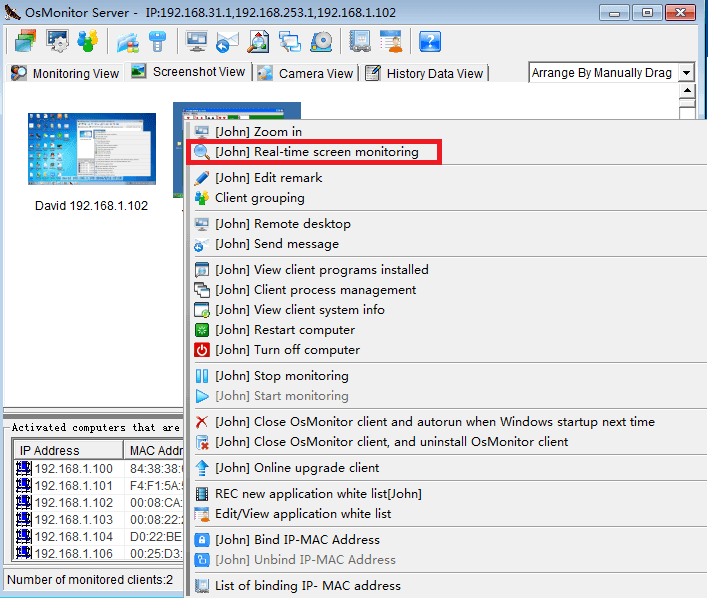
It is not hard to tell what OsMonitor does from its name -- a software that monitors operating systems. In short, we provide a convenient solution for companies whose employees extensively use computers for work. The basic features of OsMonitor can be concluded as monitoring and/or restricting what the employees do during working hours. Designed solely as software, there is no need to install or modify any hardware for OsMonitor to work. It can accurately log the time that each employee spends on different software or website each month, together with the exact website addresses logged. Restrictions such as no gaming or video streaming during work hours can be easily set to ensure everyone focuses on their work. You can also set it up in a way that only allows the employees to access work-related websites. USB devices such as USB flash drives can be prohibited, and so do large data downloads that occupy bandwidth. Moreover, different monitoring and restriction strategies can be set for different departments, giving you the most flexibility.
OsMonitor employee monitoring software does not involve deployment mode, since its implementation principle is C/S mode, and various functions are realized through the client-side deployed on the computer. In this mode, the server installation and deployment have no special requirements for the network environment, therefore making the software suitable for small and medium-sized companies that do not have professional IT technicians. Having been optimized for Windows 11, OsMonitor continues to serve thousands of users worldwide and strives to provide the best experience for our valued customers.