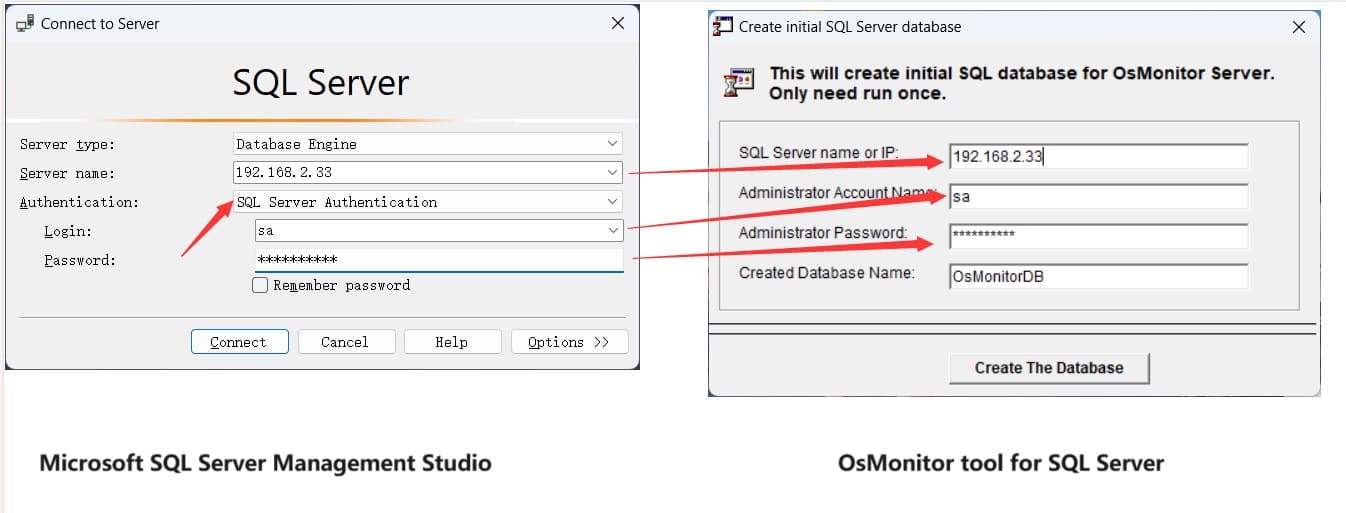
Picture this: you’re running a business, juggling a dozen priorities, and wondering how your team is spending their time behind those screens. Are they grinding away on projects, or are they sneaking in a quick scroll through social media? It’s a question every business owner or IT manager has asked at some point. That’s where employee activity monitoring software steps in—not to play Big Brother, but to give you a clear, actionable peek into what’s happening on company computers. And when it comes to a tool that’s fast, simple, and won’t bog down your systems, OsMonitor stands out like a breath of fresh air.
Let’s dive into why OsMonitor deserves a spot on your radar. This isn’t about turning your workplace into a surveillance state—it’s about understanding workflows, boosting efficiency, and keeping things on track. With a software package so small it fits under 4MB (and a client side under 1MB), OsMonitor proves you don’t need a heavyweight to get heavyweight results.
Why Employee Activity Monitoring Software Matters
In today’s world, where remote work and hybrid setups are the norm, knowing how time and resources are used is more crucial than ever. Employee activity monitoring software isn’t just about catching someone slacking off—it’s about spotting bottlenecks, identifying unproductive habits, and ensuring your team has the tools they need to succeed. For instance, if half your staff is spending hours on non-work websites, maybe it’s time for a chat about priorities—or a tweak to your internet policies.
OsMonitor gets this. It’s built from the ground up to track what’s happening on Windows computers (every version, from XP to 11) without slowing them down or making employees feel like they’re under a microscope. The best part? It’s so intuitive you’ll be up and running in minutes—no thick manual required.
OsMonitor: Tiny Package, Big Impact
What makes OsMonitor different? For starters, its size. Most employee activity monitoring software comes with bloated installs—tens or hundreds of megabytes that hog resources and frustrate users. OsMonitor, though? It’s a featherweight at under 4MB total, with the client side clocking in at less than 1MB. That means lightning-fast deployment and zero noticeable impact on your team’s computers. Employees won’t even know it’s there unless you want them to—by default, it runs silently, but you can flip a switch to show a tray icon if transparency’s your thing.
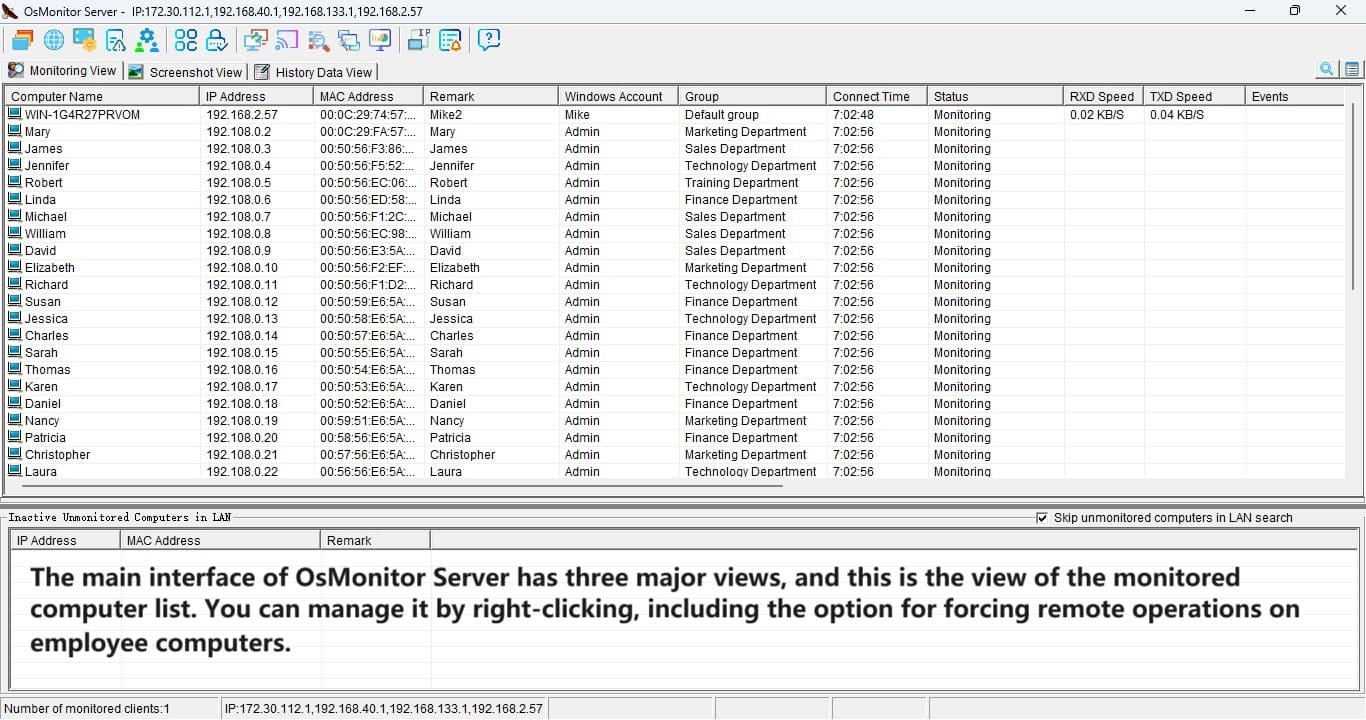
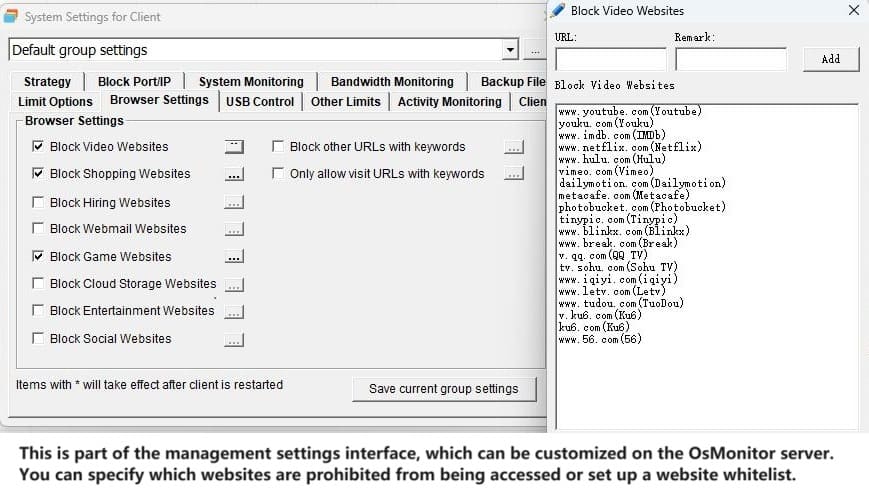
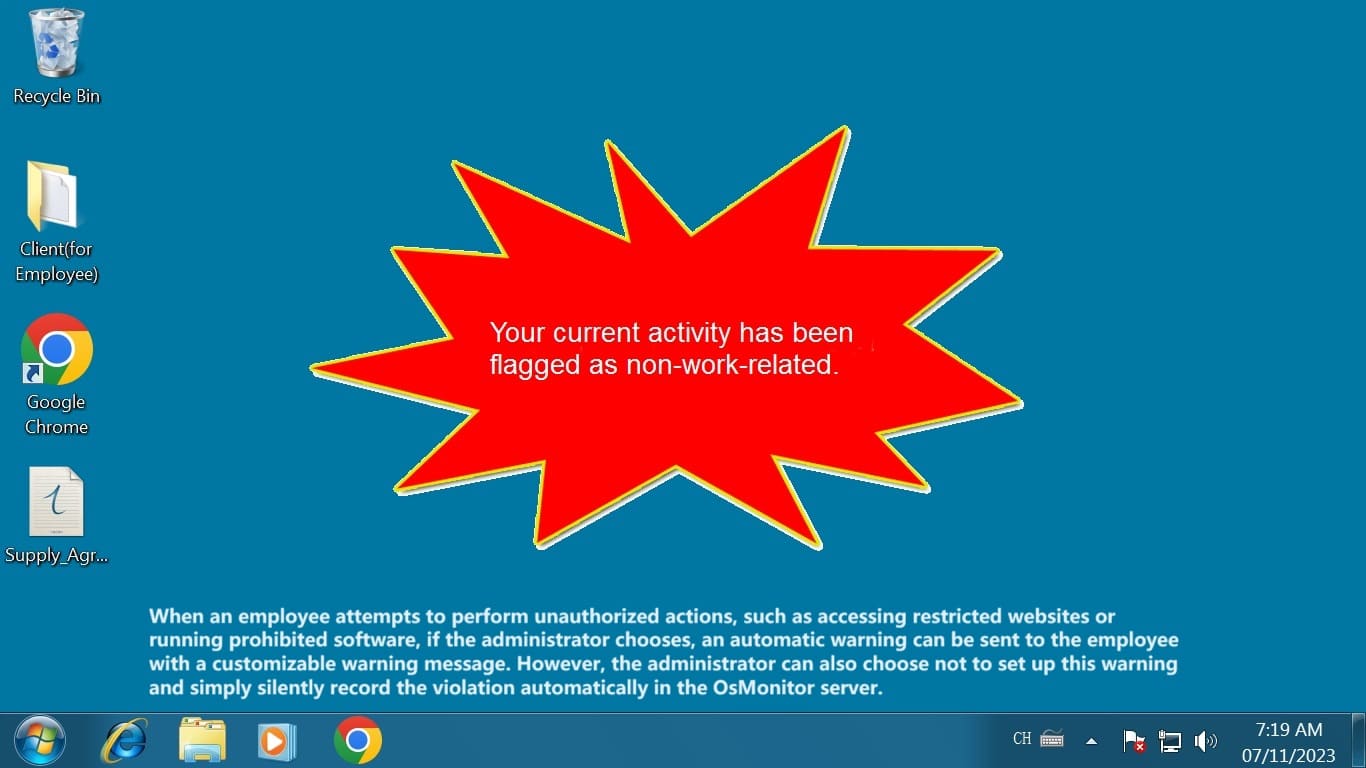
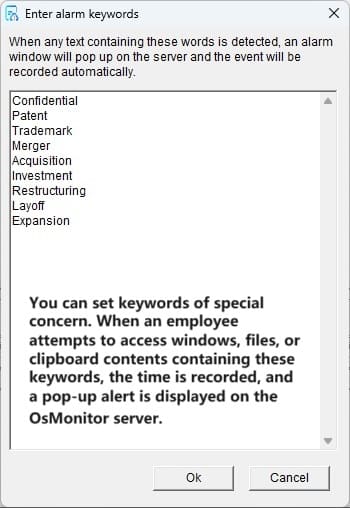
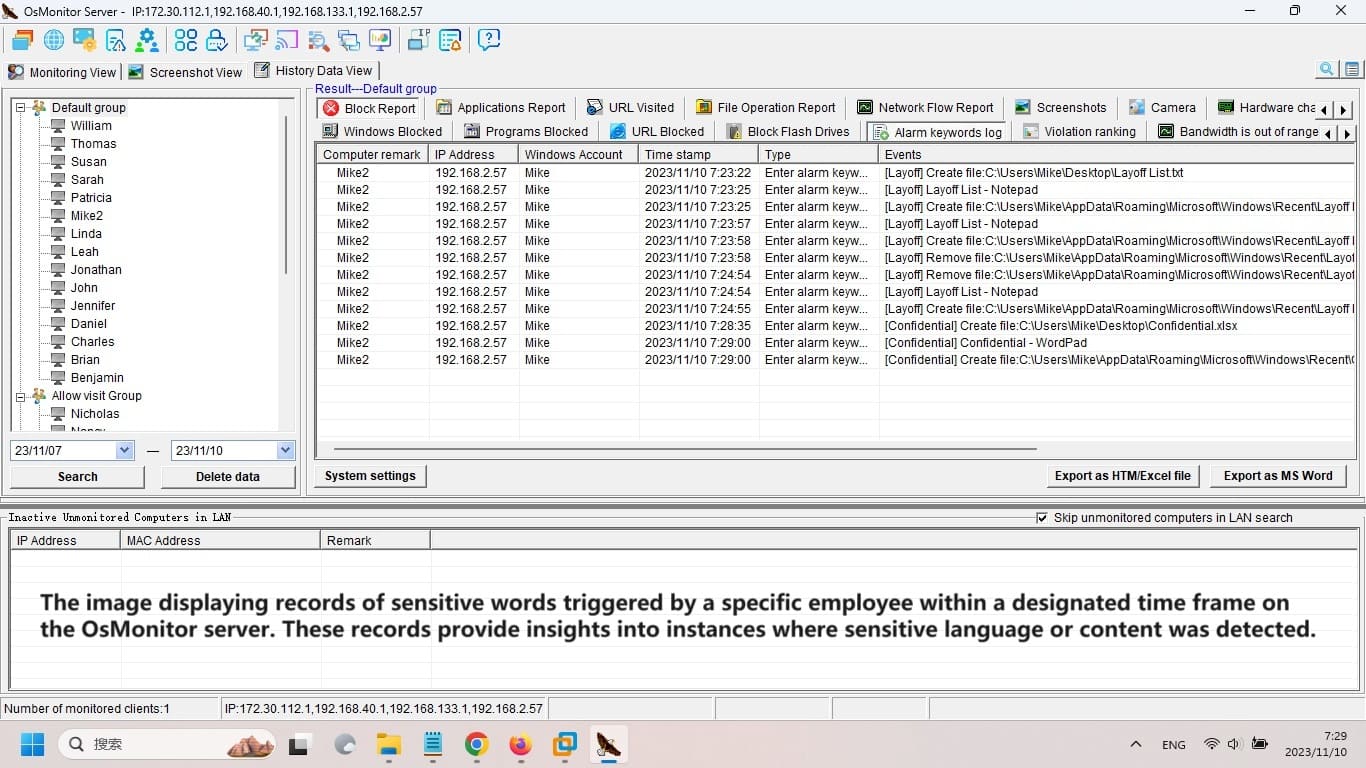
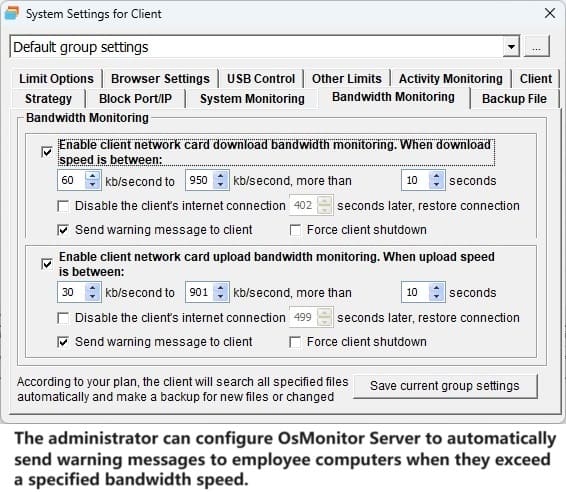
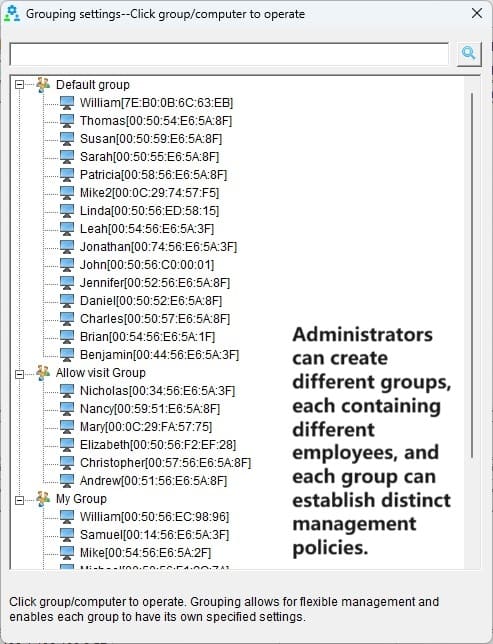
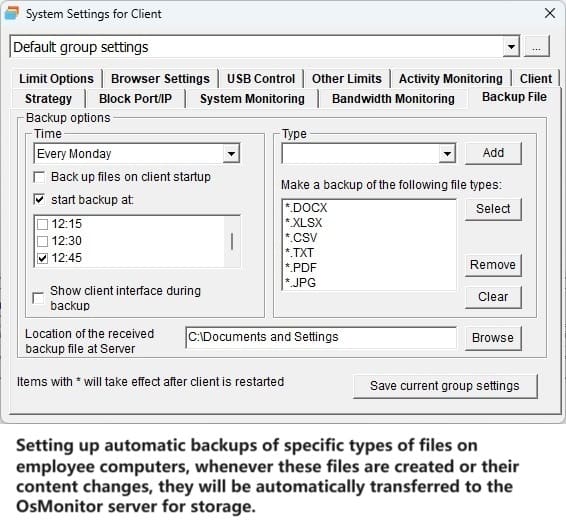
And don’t let the small size fool you. This tool packs a punch. It tracks everything from screen activity and app usage to website visits and file movements. Want to know who’s copying files to a USB drive or chatting away on instant messengers? OsMonitor’s got you covered with detailed logs and reports. It even lets you block distractions like games, shopping sites, or USB access, keeping everyone focused on what matters.
Hands-On Control, Made Simple
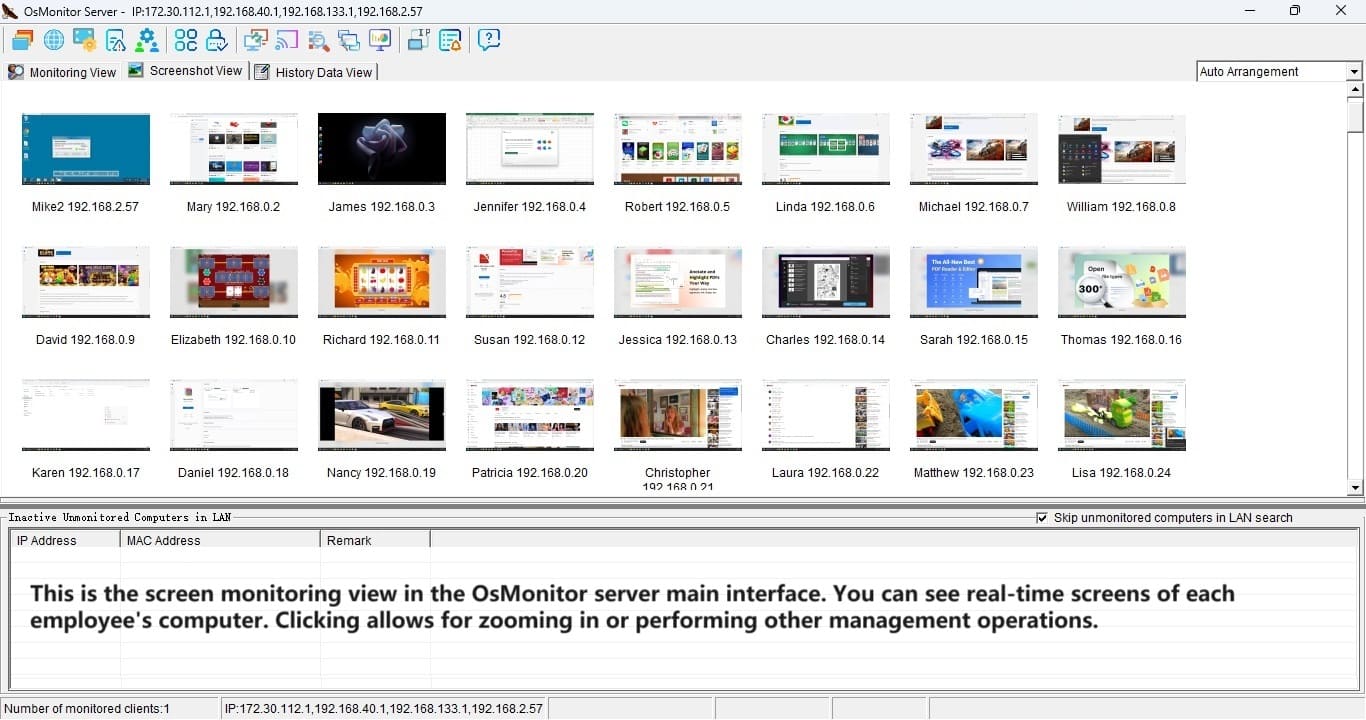
Imagine sitting at your desk and remotely peeking at an employee’s screen—like you’re right there, without the awkward shoulder-tap. OsMonitor’s remote desktop feature makes it possible. Need a Word doc from someone’s computer? It’ll grab it and save it to the server automatically. You can even shut down or restart machines remotely, end rogue apps, or send a quick message to the team (or just one department). It’s management made effortless, all from one central hub.
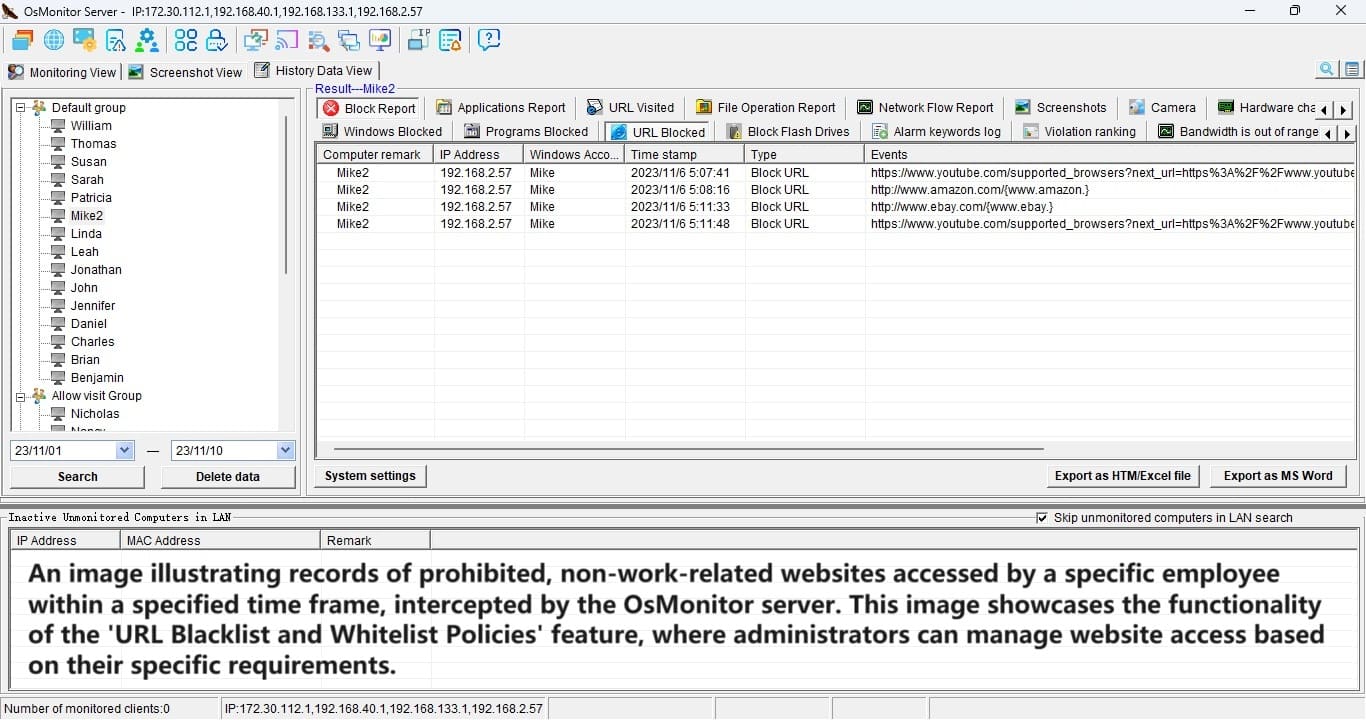
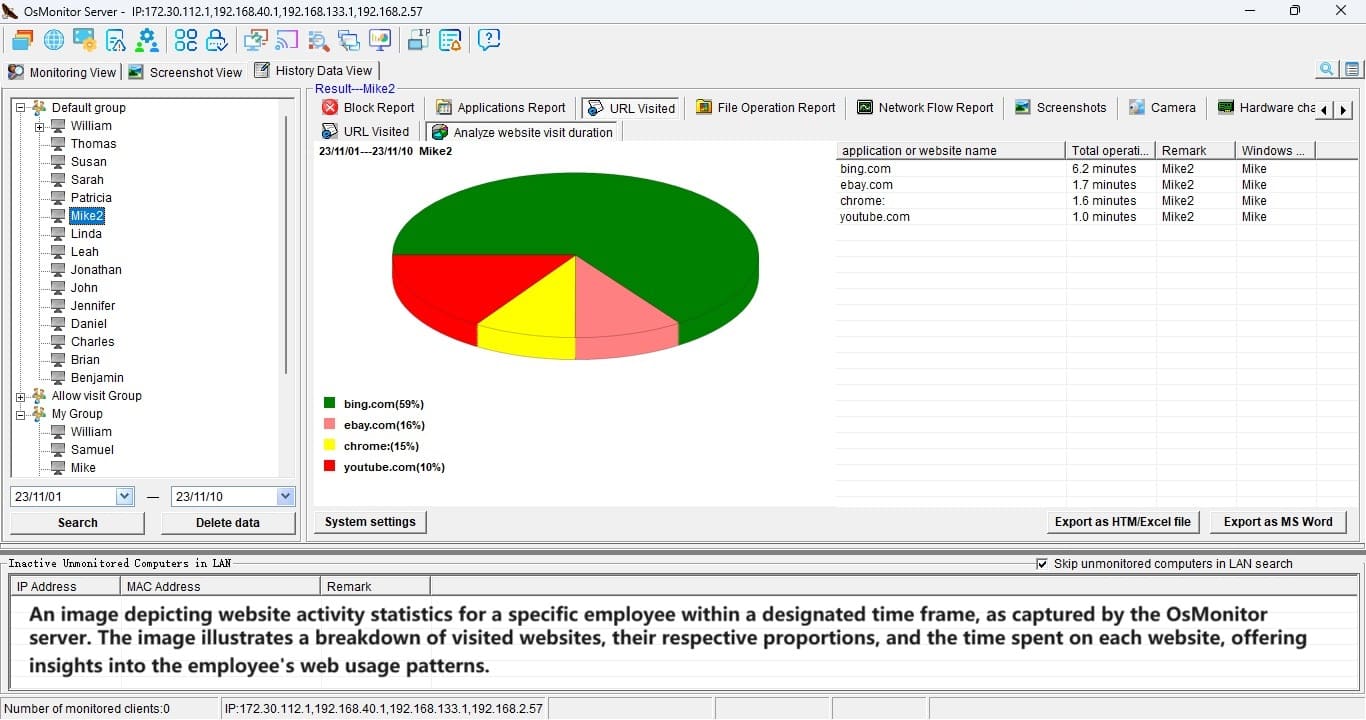
The reports OsMonitor churns out are a goldmine. You’ll get breakdowns of app usage, website time, clipboard history, and more—think of it as a productivity dashboard. One user shared how they spotted an employee spending 40% of their day on YouTube. After a friendly chat and some site-blocking tweaks, that time dropped to near zero, and output soared. It’s not about punishment—it’s about clarity.
Balancing Oversight with Trust
Now, let’s be real: monitoring can feel like a tricky topic. Some employees might bristle at the idea of their work being tracked. But here’s the thing—when you’re open about why you’re using employee activity monitoring software and how it benefits the team, resistance often melts away. OsMonitor isn’t about sneaking around; it’s about creating a workplace where everyone’s on the same page. Tell your team it’s there to streamline processes or cut distractions, and pair it with fair policies. You might be surprised how quickly they get on board.
Take a small marketing firm as an example. Their IT manager rolled out OsMonitor to curb excessive personal browsing during crunch time. After explaining it was about keeping projects on track—not micromanaging—the team adapted. Within a month, deadlines were tighter, and the mood was lighter because the work was getting done.
Why OsMonitor Excels Over the Competition
Unlike clunky alternatives, OsMonitor doesn’t demand extra hardware or a PhD to figure out. It’s pure software, designed to slot into your existing setup with zero fuss. And the pricing? One-time purchase, no recurring fees. Compare that to subscription-based tools that nickel-and-dime you year after year, and it’s a no-brainer. Plus, it’s built to run on any Windows system, so whether your office is rocking ancient XP machines or shiny Windows 11 rigs, you’re good to go.
The ease of use is a game-changer. Install the server on your machine, slap the tiny client on employee computers, and you’re off. No convoluted menus, no steep learning curve—just results. One IT manager called it “the monitoring tool you forget you’re using because it just works.”
Ready to See It in Action?
Here’s the kicker: OsMonitor offers a free trial. No strings, no risk—just a chance to see how it fits your business. Imagine having a crystal-clear view of your team’s digital habits by the end of the week. Are they crushing it, or is there room to tweak? You won’t know until you try. Head to the OsMonitor website, snag the download, and take it for a spin. At under 4MB, it’ll be installed before your coffee’s cold.
Employee activity monitoring software like OsMonitor isn’t about distrust—it’s about empowerment. It hands you the insights to run a tighter ship, free up resources, and let your team shine. For business owners, execs, and IT pros who want efficiency without the headache, this little tool might just be the secret weapon you’ve been looking for. Give it a shot—you’ve got nothing to lose and a whole lot of productivity to gain.